Bitcoin Whitepaper
Bitcoin: A Peer-to-Peer Electronic Cash System
Introduction
Satoshi Nakamoto proposes an overarching solution to double spending problem using a peer-to-peer network which supports an electronic payment system based on cryptographic proof instead of trust unlike the the method used by financial institutions. A computational proof of the chronological order of transaction is generated by p2p distributed timestamp server. The reversal of transaction will be computationally impractical unless more than 50% of nodes are not intending to attack the network.
Transactions
Each transaction is clubbed with the hash of the previous transaction and public key of next owner then signed by the person making this transaction. This forms a chain of transactions. This chain of digital signatures are called electronic coin. Solving double spending problem without any mediating third-party requires a node to be aware of all the transactions.
- The transactions must be publicly announced.
- All participants must agree on a single chronological order of all transactions.
Timestamp Server
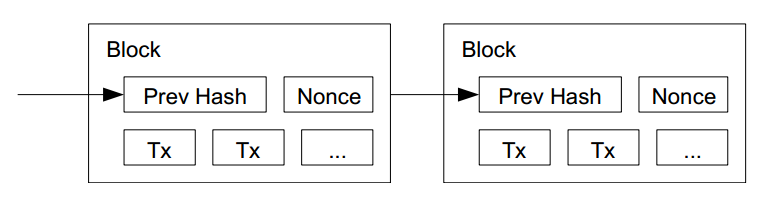 Timestamp server generates a hash of the current block, it also includes timestamp of previous block, hence forming a chain.
Timestamp server generates a hash of the current block, it also includes timestamp of previous block, hence forming a chain.
Proof of work
The Proof-of-Work[PoW] involves guessing a nounce value which can generate a hash which starts with a required amount on zero bits. The block cannot be changed without redoing the work. This implies that to modify a past block, an attacker would have to redo the PoW for that block and all the blocks after it. Average work required is exponential in the number of zero bits required. PoW difficulty increases if blocks are being generated too fast.
Y=H ( X || k )
There exist no efficient algorithm to find value of k(nounce).
Network
New transactions are broadcasted to all nodes, all the nodes collect new transactions into a block and try to find PoW for that block. When PoW is found, the block is broadcasted to all the nodes. The block is accepted by the nodes if all the transactions in the block are valid and not already spent. The hash of the accepted block is considered as previous hash. Nodes always consider longest chain to be the correct one and work on extending it.
Incentive
Just like gold miners adding gold to the circulation, the bitcoin miners too get paid as block reward when they are successful in their PoW, that means, with each new block, the bitcoin in the economy increases.The incentive can also be funded with transaction fees. The first transaction in a block is a special transaction that starts a new coin owned by the creator of the block.
Saving disk space
Instead of storing whole Merkle Tree, we can stubbing off the branches off the tree and keeping the block header with no transactions. The hash value in the block header keeps the integrity of all its sub-branches and transactions.
Payment Verification
A transaction can be verified by a user without running a full node network. It just has to keep a copy of block headers of the longest PoW chain. The user cannot check for validity of the transaction by himself because he won’t be having all the transactions with himself. He can just see that the transaction is a part of longest chain and this confirms that the transaction is valid. Verification requires executing only single hash.
Privacy
Privacy can be maintained by keeping public keys anonymous. It is advisable to use a new key pair for each transaction to keep them from being linked to a common owner.
Security
An attack can only try to change one of his own transactions to take back money he recently spent. The probability of a survival of a dishonest chain is fairly low.